
As a CTO with 25 years of cybersecurity experience, I am never at ease with the state of cybersecurity. It’s not because we’re not doing our jobs, it’s just that our modern-day businesses operate as part of a larger business ecosystem and I am concerned about the additional risks operating like this brings to an organization. Specifically, I am talking about third-party risk.
It is a hidden weakness that may undermine even the most formidable organizations, much like Superman’s kryptonite. Financial losses, operational disruptions, and reputational damage can occur as a result of a vendor, supplier, or contractor’s single slip-up, leaving you feeling helpless.
Why is third-party risk so potent? It’s simple:
- Increased Reliance on External Partners: We outsource more than ever before, from IT infrastructure to marketing campaigns. This expands our attack surface, making us vulnerable to the weaknesses of others. It’s the weakest link principle, you are “only as strong as its weakest link.”
- Lack of Transparency: When it comes to the security and operations of third parties, we don’t always have complete control.
- Complex Ecosystem: The web of third-party relationships can be intricate and ever-changing, making it difficult to track and manage risk effectively
I am not trying to instill fear in you, but the potential fallout is no joke:
Operational Disruptions
A critical vendor outage can cripple your entire business, costing you revenue and damaging customer relationships.
Production at some of Stellantis’ North American assembly plants were offline for approximately 3 days.

Source: BleepingComputer
Damage to Reputation
Hearing of your outside party’s cybersecurity incident can swiftly tarnish your brand, making it hard to entice consumers and investors.
The public disclosure of the hack that affected more than 18,000 companies and many government bodies caused SolarWinds’ stock price to plummet.
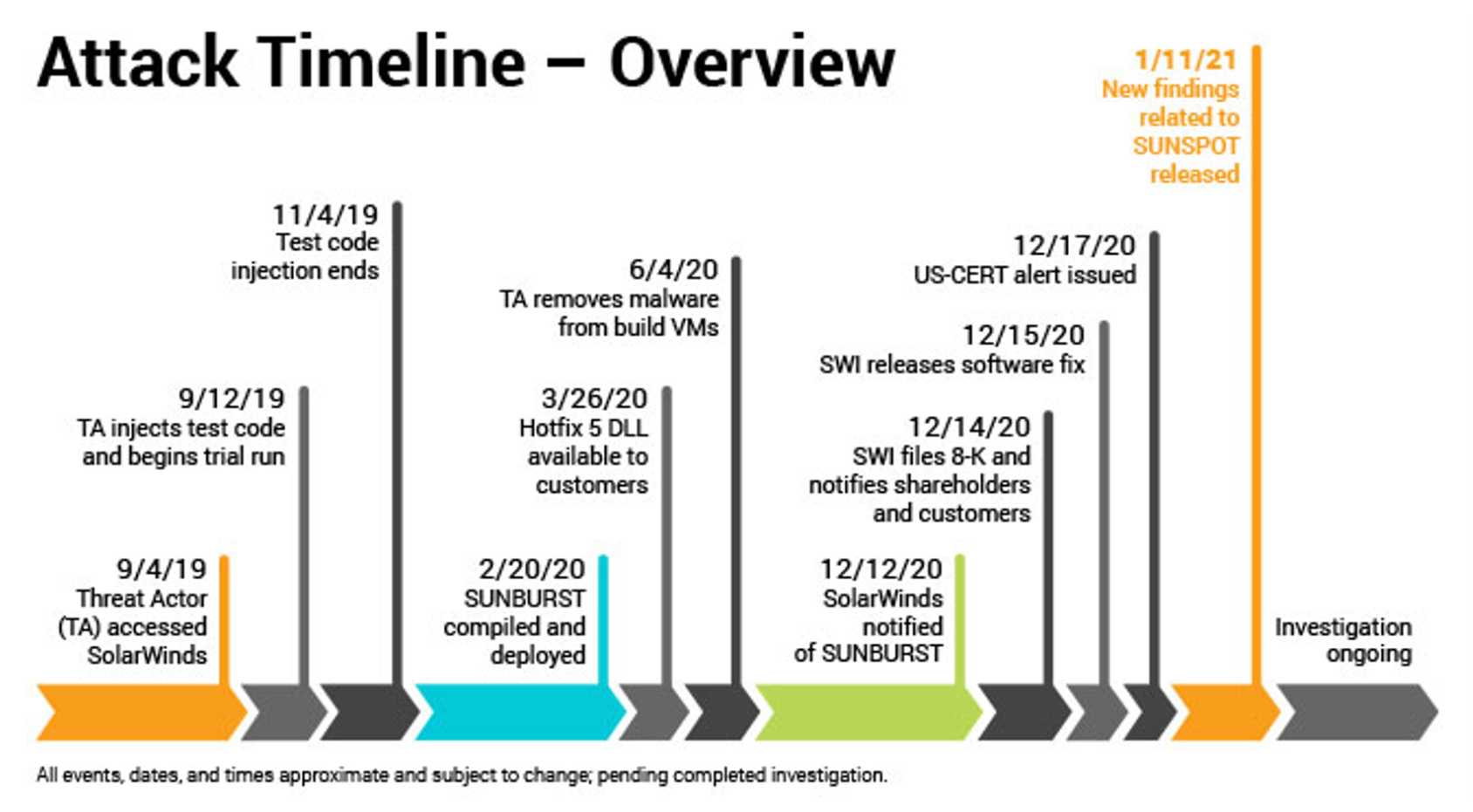
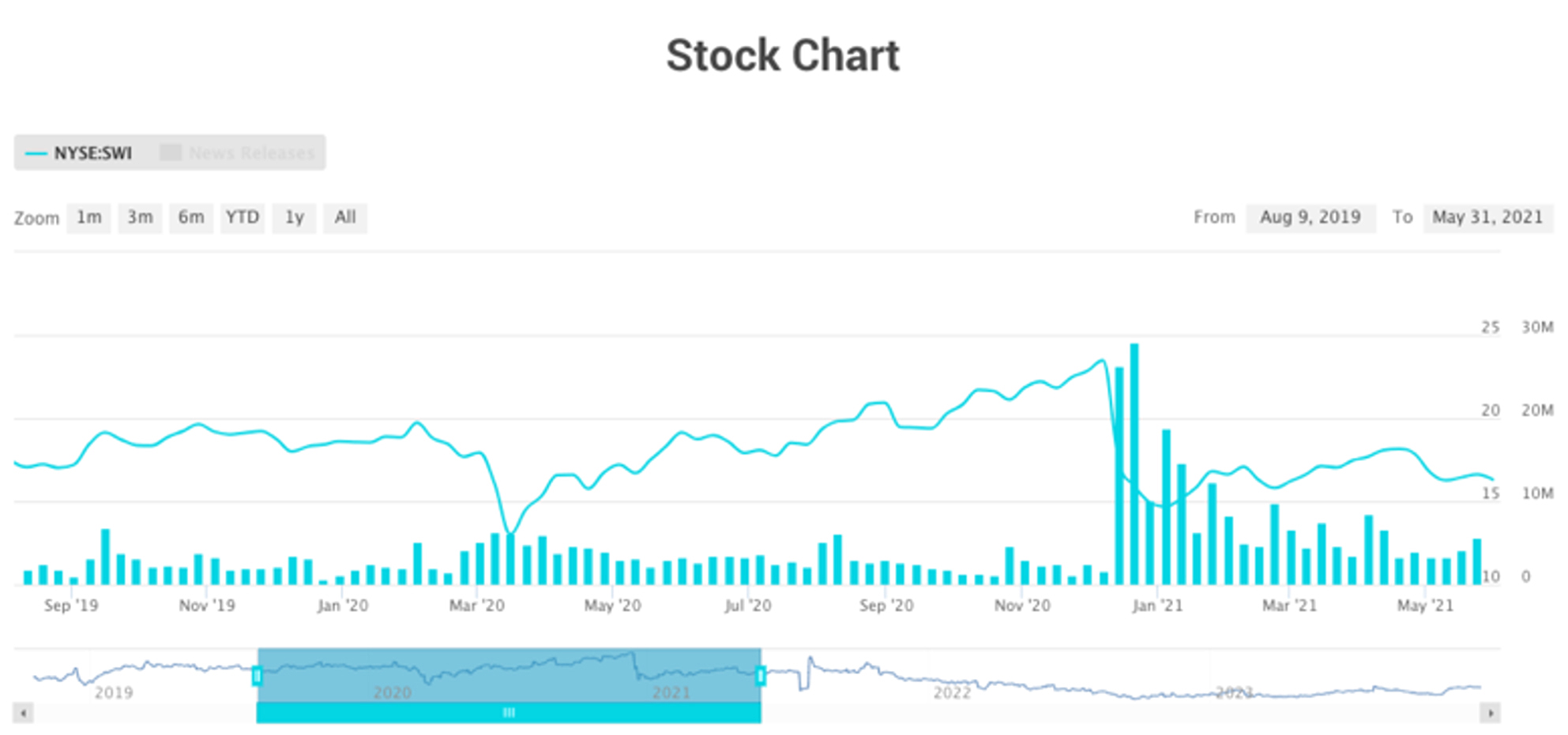
Source: SolarWinds
So, what can we do to avoid the kryptonite kiss of death? Here’s my playbook:
- Proactive Due Diligence: Thoroughly examine potential risks before onboarding any third party as part of proactive due diligence. Look at their security measures, regulatory compliance, and financial soundness. Do not merely mark the box; delve deeply.
- Contractual Safeguards: Craft watertight contracts that clearly define risk ownership, incident response protocols, and termination clauses. Make sure you’re not left holding the kryptonite bag.
- Always Be Watching: Never Leave It Alone. Keep a close eye on how well your third parties are doing and how secure they are. To remain one step ahead of possible dangers, make use of technological and intelligence-based solutions.
- Open Communication: Foster open communication channels with your third parties. Encourage them to share security updates, incident reports, and any concerns they may have. Remember, we’re all in this kryptonite fight together.
- Build a Culture of Awareness: Educate your employees about third-party risk and how their actions can impact it. Encourage them to report suspicious activity and be vigilant about phishing attacks and social engineering scams.
If you follow these steps, you can make third-party risk work for you instead of against you. Your operational efficiency, competitive edge, and organization’s resilience can all be improved with a well-managed ecosystem of third parties.
Remember, in the game of risk management, Superman might be able to fly, but a proactive approach is the real magic bullet. So, go forth, brave risk managers, and conquer the kryptonite!
Just a friendly reminder to include kryptonite-resistant underwear in your budget... I mean, cyber insurance. Being cautious is preferable than being unprepared.
Sources:
1. Ponemon Institute and Shared Assessments survey - Third-Party Risk Management Benchmarking Study 2019
2. Predictions 2022: Cybersecurity, Risk and Privacy, Forrester Research, Inc., Oct. 28, 2021
