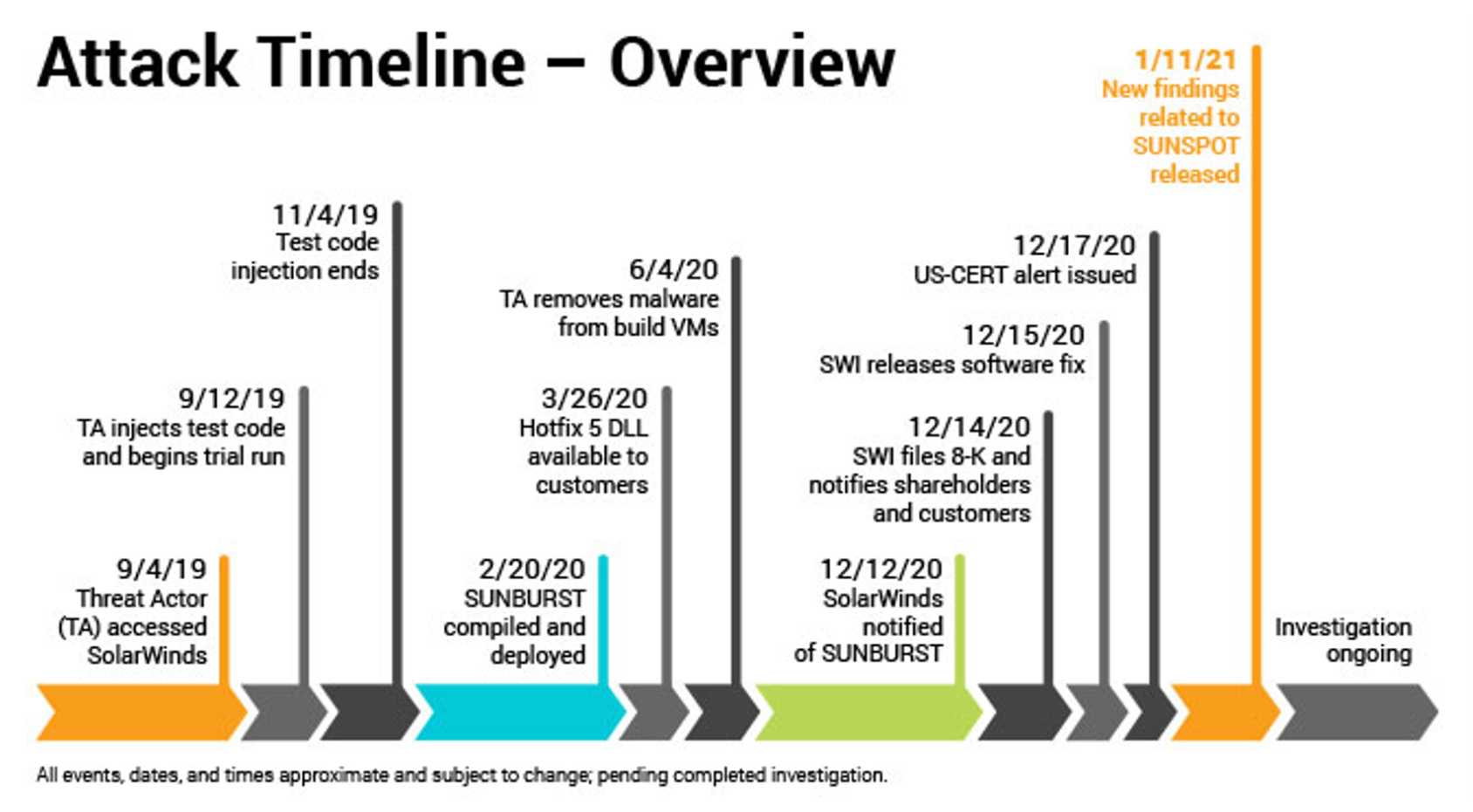
The National Institute of Standards and Technology (NIST) recently unveiled the second iteration of its cybersecurity framework, commonly referred to as NIST Framework 2.0. This updated version introduces significant enhancements and changes that reflect the evolving landscape of cybersecurity threats and the need for more adaptive and robust security measures. The original framework, established to provide organizations with a comprehensive set of guidelines for managing cybersecurity risk, has been widely adopted across various sectors. However, as cyber threats have grown in complexity and frequency, the need for an updated framework became evident. This blog will explore the key updates in NIST Framework 2.0 and highlight the major differences from its predecessor.
1. Enhanced Emphasis on Privacy and Supply Chain Risk Management
One of the most notable updates in NIST Framework 2.0 is the increased emphasis on privacy and supply chain risk management. The original framework touched on these areas, but the latest version provides more detailed guidance, acknowledging the interconnected nature of today’s digital ecosystems. Organizations are encouraged to adopt a more holistic approach to cybersecurity, considering not only their internal processes but also how they interact with partners, suppliers, and third-party service providers.
2. Introduction of New Categories and Subcategories
NIST Framework 2.0 introduces new categories and subcategories that address emerging technologies and threat vectors. For instance, there is now more explicit guidance on cloud security, mobile device management, and the Internet of Things (IoT). These additions are designed to help organizations navigate the security challenges associated with these technologies, which were not as prevalent or critical when the original framework was developed.
3. Focus on Cybersecurity Resilience
Another significant shift in NIST Framework 2.0 is the increased focus on cybersecurity resilience. While the original framework emphasized identifying, protecting, detecting, responding, and recovering from cybersecurity incidents, the new version goes further by stressing the importance of resilience throughout these stages. This means not only reacting to cyber threats but also ensuring that operations can continue during and after an attack. The updated framework encourages organizations to develop and maintain systems that are not only secure but also resilient to disruptions.
4. Improved Accessibility and Flexibility
Recognizing the wide range of organizations that use the framework, from small businesses to large enterprises and government agencies, NIST Framework 2.0 is designed to be more accessible and flexible. The language has been simplified where possible to make the guidelines more approachable for non-experts. Additionally, the framework offers more examples and templates to assist organizations in implementing the recommended security measures. This inclusivity ensures that organizations of all sizes and sectors can effectively apply the framework to improve their cybersecurity posture.
5. Strengthened Alignment with Other Standards and Frameworks
NIST Framework 2.0 aims for better alignment with other international standards and cybersecurity frameworks, such as ISO/IEC 27001 and the CIS Controls. This harmonization is beneficial for organizations that adhere to multiple standards, as it simplifies compliance efforts and strengthens overall cybersecurity practices. By ensuring compatibility with other widely recognized frameworks, NIST makes it easier for organizations to adopt a comprehensive and cohesive approach to managing cybersecurity risk.
In Summary
Comparing NIST Framework 2.0 to its predecessor, the most significant differences lie in its broader scope, which now includes detailed guidance on privacy and supply chain risks, and its adaptability to emerging technologies. The emphasis on resilience and the efforts to make the framework more accessible and aligned with other standards demonstrate a forward-thinking approach to cybersecurity. The release of NIST Framework 2.0 marks a significant milestone in the evolution of cybersecurity standards. By addressing current challenges and providing clear, actionable guidance, the framework is a vital resource for organizations aiming to bolster their cybersecurity measures. As cyber threats continue to evolve, staying abreast of updates like NIST Framework 2.0 is crucial for organizations committed to safeguarding their operations and assets against cyber risks.
How Impelix IMPACT Can Help With Compliance
With the modifications to the NIST Framework, you may be wondering how they impact your cybersecurity maturity. The IMPACT platform from Impelix approaches compliance through a data-driven strategy. By integrating all the technologies in your stack and collecting telemetry, IMPACT can provide a real-time snapshot of your compliance progress with no effort. You will be able to check against common frameworks such as NIST CSF, ISO 27001, CIS CSC, and NIST 2.0, which will be introduced to the platform shortly. This allows you to assess your organization’s preparedness against a cybersecurity framework in a cost-effective manner.